| Name | Flags | Card. | Type |
Description & Constraints

|
|---|---|---|---|---|

|
AuditEvent | |||

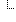
|
Slice: Unordered, Open by pattern:type | |||



|
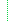
Content/Rules for all slices | |||



|
Slice: Unordered, Open by value:url | |||




|
S | 0..* | CodeableConcept |
AuditEvent.agent Assurance Level
URL: https://profiles.ihe.net/ITI/BALP/StructureDefinition/ihe-assuranceLevel Binding: todo ( preferred ) |



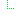
|
S | 0..* | Identifier |
AuditEvent.agent other identifiers
URL: https://profiles.ihe.net/ITI/BALP/StructureDefinition/ihe-otherId |


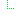
|
1..* | |||



|
S | 0..* | CodeableConcept |
AuditEvent.agent Assurance Level
URL: https://profiles.ihe.net/ITI/BALP/StructureDefinition/ihe-assuranceLevel Binding: todo ( preferred ) |



|
S | 0..* | Identifier |
AuditEvent.agent other identifiers
URL: https://profiles.ihe.net/ITI/BALP/StructureDefinition/ihe-otherId |



|
1.. | Required Pattern: At least the following | ||



|
1..* | Coding |
Code defined by a terminology system Fixed Value: (complex) |
|





|
1..1 | uri |
Identity of the terminology system Fixed Value: https://profiles.ihe.net/ITI/BALP/CodeSystem/UserAgentTypes |
|





|
1..1 | code |
Symbol in syntax defined by the system Fixed Value: UserSamlAgent |
|



|
1.. | |||




|
||||





|
S | SAML Issuer | ||





|
S | 1.. | SAML Subject.NameID | |



|
Required Pattern: true | |||



|
S | 1..1 | SAML token ID | |



|
.. 0 | |||



|
.. 0 | |||



|
S | SAML subject:purposeofuse | ||
 Documentation for this format Documentation for this format
|
||||